 |
| Courtesy of Flickr |
News Headline:
“A new strain of bird flu was recently detected in China that has killed four
of the sixteen people it infected.” As a
precaution, hundreds of thousands of chickens have been slaughtered in China to
prevent the spread of the virus. The US Center for Disease Control has been put
on high alert.
However, when it comes to cyber
threats, governments are sometimes slow to act. This is one area where bureaucratic red
tape stops anything from being done. The
fact is, “you” have to take responsibility for the safety of your identity and
information. You are the only person who can keep your internet devices from
being infected.
| The Search Results that showed every page had malware (Photo credit: |
“Did you know that in
2008, it was estimated the number of known computer viruses stood at in excess
of 1 million, an increase of 468 per cent on the previous year? Figures suggest at least five malware samples emerge on the
Internet every two minutes and 15 to 20 new Trojans are released every half
hour.” http://www.prlog.org/10814398-number-of-known-computer-viruses-exceeds-1-million.html
The figures as of 2013 are as
high as 17 million according to antivirus maker Symantec. Far from being a high priority on the minds
of government officials, in many cases the laws that do exist actually work to
prevent government cooperation. Even
within our own borders, the authorities have yet to create effective
legislation that offers any hope of curtailing the proliferation of
malware. Prosecutions against malware
developers are rare. In the meantime, cyber
criminals from hacker collectives to foreign governments are busy 24/7 cranking
out ever more insidious ways of infecting your computer.
Here Are Just a Few Headlines
June 12, 2012 ZDNet: On Sunday Microsoft reported that “… some components of the
malware have been signed by certificates that allow software to appear as if it
was produced by Microsoft. http://www.zdnet.com/blog/btl/the-5-worst-computer-viruses/79014
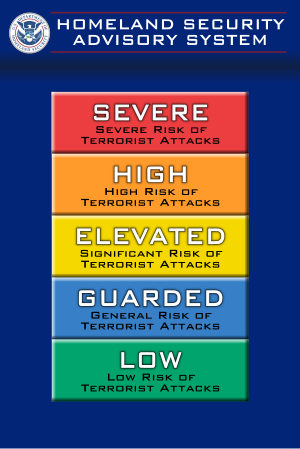
| Homeland Security Advisory System scale. |
Dec. 26, 2012: New viruses that are disguised to look like a government program have
been spreading around the world. The new type of virus generally blocks users
from accessing their desktop, documents, and programs until the user pays a
ransom (generally a hundred dollars or more) to the cyber criminals who created
the virus. http://www.prweb.com/releases/2012/12/prweb10267341.htm
Jan. 13, 2013: The US Department of Homeland Security
is advising people to temporarily disable Java software on their computer to
avoid potential hacking attacks.
Once inside your computer,
hackers can do everything from directing you to clone sites designed to get you
to reveal your passwords, to activating your computer’s camera in order to spy
on you, to holding your system hostage, or even hijacking your machine in order
to infect yet more systems. The good
news is that with the right combination of software and a little online
discipline, preventing all but the most concerted of hacking efforts is
relatively simple to accomplish. The bad
news is that once infected, your system and your life may never be the same.
Ammunition to Keep Yourself Safe
| English: Full Ready.gov logo with tagline and trademark notice. |
While most people have at
least an antivirus program working on their PCs and laptops, it isn’t at all
unusual for them to have no protection on tablets and especially smartphones. Cyber-criminals are well aware of this
vulnerability, so you need to plug this hole in your defenses right away if you
hope to avoid being hacked. (You also
need to update most anti-malware packages and scan your system weekly to keep
up to date.)
There are many types of
malware that can infect your computer, but the types that can steal your data
are simply called "information stealers." They are made up of things
like keyloggers, screen recorders and memory scrapers. They perform a variety
of tasks, from recording what keys you press to taking screenshots of your
desktop at random intervals. This information is then sent to the malware's
designer, showing them whatever you typed or viewed on your computer. Using
this method, a hacker can steal any data from computer passwords to credit card
numbers. http://science.opposingviews.com/can-computer-viruses-steal-credit-card-information-19380.html
Another defense layer you can
add is using website rating plugin’s to your browser. Browser plugin’s like Web
of Trust uses a stoplight rating system where suspicious sites are flagged with
a red light and trusted sites are given the green. If you click on a site flagged with a red
light, that’s like leaving your car in the parking lot of a shopping mall with
the ignition running and a “Steal Me” sign on the windshield. Site advisory systems will only warn and not
prevent you from accessing potentially harmful websites.
There’s a Trojan (App) for That
| Malware logo Crystal 128. |
"The humorous IT security expert, who sports numerous
tattoos and has a penchant for heavy metal music, can hack into your mobile
phone with a single SMS. He can then
remotely listen to your calls, read text messages and even access the password
to your online bank account.
“'It’s creepy, isn’t it?' said Ferguson, who is global
vice-president for security research for IT firm Trend Micro, as he
demonstrated the hack. Yet, many users still refused to believe how vulnerable
they are when they use mobile devices, he added. http://thestar.com.my/news/story.asp?file=/2013/4/9/asia/12943938&sec=asia
In order to prevent picking up
these unwanted hitchhikers, only download apps and software from trusted
vendors. You also need to research app
review sites such as C|Net.com, Tucows.com, iTunes.com and GooglePlay.com in
order to find out if an app is reputable. Always look for apps that have
thousands of subscribers. Stay away from new apps; they just could be a wolf in
sheep's clothing. Purchase and use antimalware software for your mobile phone and
tablet. Many mobile security suites will
scan your apps as they are downloaded, preventing viruses and other forms of
malware from attaching themselves to your devices easily.
Ignoring Your Computer's Symptoms Won’t Make the Problem
Go Away
 |
| Get your Free e|Book Above. |
If you like this article, you can find more by typing “internet security" in the search box at the top left of this blog. If you found this article useful, share it with your friends, families and co-works. If you have a comment related to this article, leave it in the comment sections below.
Thanks for sharing your time with me.
Since 1995, Carl Weiss has been helping clients succeed online. He owns and operates several online marketing businesses, including Working the Web to Win and Jacksonville Video Production. He also co-hosts the weekly radio show, "Working the Web to Win," every Tuesday at 4 p.m. Eastern on BlogTalkRadio.com.
If you'd like a FREE Copy of our eBook,
"Internet Marketing Tips for the 21st Century," please fill in the
form in the upper right-hand sidebar, where you will receive instant access to
our eBook. Your information is always kept private and is never sold.
Thanks for sharing your time with me.
Since 1995, Carl Weiss has been helping clients succeed online. He owns and operates several online marketing businesses, including Working the Web to Win and Jacksonville Video Production. He also co-hosts the weekly radio show, "Working the Web to Win," every Tuesday at 4 p.m. Eastern on BlogTalkRadio.com.



No comments:
Post a Comment